How does mspy work on android – Embark on a journey into the digital world with
-how does mSpy work on android*, an enchanting exploration of a device that gives a singular perspective on cellular gadget monitoring. Think about a world the place understanding the inside workings of a tool isn’t just a technical endeavor however a story journey, crammed with sudden twists and turns. This information is not simply concerning the mechanics; it is concerning the story behind the expertise, the alternatives customers make, and the moral crossroads they face.
We’ll unravel the mysteries of set up, beginning with the preliminary steps and the granting of vital permissions. Then, we are going to dive into knowledge assortment, revealing how mSpy gathers data from name logs, textual content messages, location knowledge, and social media. You’ll uncover the app’s options, from monitoring shopping historical past to monitoring put in purposes and wielding distant management capabilities. Moreover, we’ll look at stealth mode and its impression, delving into the person interface, compatibility, gadget necessities, authorized issues, and troubleshooting widespread points.
Every step of the way in which, you will achieve a complete understanding of the expertise’s capabilities and its implications.
Set up Course of on Android: How Does Mspy Work On Android
Embarking on the journey of putting in mSpy on an Android gadget is akin to making ready for a mission – a mission of digital guardianship. This course of, whereas easy, calls for cautious consideration to element to make sure seamless operation and discretion. Consider it as organising a safe base camp earlier than venturing into the digital wilderness.
Preliminary Steps for Set up
The preliminary section includes buying the mSpy utility file, also known as an APK (Android Bundle Package). This file is the important thing to unlocking the monitoring capabilities.
- First, you have to to acquire the APK file, usually via a direct obtain hyperlink offered by mSpy after your subscription is activated. This hyperlink is normally despatched to the e-mail deal with you registered with or accessible via your on-line account.
- Subsequent, on the goal Android gadget, you need to allow the set up of purposes from “Unknown Sources.” It is a vital step as a result of mSpy isn’t accessible on the Google Play Retailer. To do that, navigate to the gadget’s “Settings,” then “Safety” or “Privateness,” and toggle the choice to permit installations from unknown sources. This primarily grants the gadget permission to put in apps from sources aside from the official Google Play Retailer.
- Lastly, find the downloaded APK file (normally within the “Downloads” folder) and faucet on it to start the set up. Observe the on-screen prompts, which can information you thru the method. The prompts will usually ask you to simply accept the app’s permissions.
Process for Granting Permissions
Granting permissions is like handing over the keys to totally different areas of a digital dwelling. Every permission permits mSpy to entry particular options and knowledge on the goal gadget.
- Throughout the set up, mSpy will request a collection of permissions. These permissions are important for the appliance to operate accurately.
- You may be prompted to grant entry to varied functionalities, together with contacts, name logs, SMS messages, location knowledge, and entry to the gadget’s storage. These permissions allow mSpy to gather and transmit the related data.
- Fastidiously overview every permission request. Granting the mandatory permissions is essential for the appliance to operate absolutely, however be conscious of the entry you’re offering.
- Some Android variations might require further steps, resembling granting “Utilization Entry” or “Accessibility Service” permissions. These permissions enable mSpy to observe utility utilization and different actions on the gadget.
Hiding the mSpy Software Icon
Concealing the mSpy utility icon is akin to using a cloak of invisibility. It ensures the appliance operates discreetly, making it much less prone to be detected by the gadget person.
- After the set up is full and all permissions are granted, you’ll usually be given the choice to cover the mSpy utility icon. That is normally completed throughout the setup course of.
- Find the choice to cover the icon inside the mSpy utility settings. The precise wording might differ, however it can usually contain a toggle or a checkbox.
- After you have chosen the choice to cover the icon, the appliance will disappear from the gadget’s app drawer and residential display. Nonetheless, it can proceed to run within the background, monitoring the gadget’s actions.
- To entry the appliance later, you’ll usually want to make use of a secret code, a hidden URL, or a selected dial code, which you’ll arrange throughout the preliminary configuration. Maintain this entry technique safe and personal.
Android Model Compatibility
Compatibility is the cornerstone of performance. Guaranteeing mSpy capabilities flawlessly throughout numerous Android variations is paramount. The desk under particulars the supported Android variations and their compatibility with mSpy. Keep in mind that compatibility can change with updates, so it is at all times clever to seek the advice of the official mSpy web site for probably the most up-to-date data.
| Android Model | Compatibility | Key Options Supported | Notes |
|---|---|---|---|
| Android 14 | Absolutely Appropriate | Name Monitoring, SMS Monitoring, GPS Location, App Exercise, Social Media Monitoring (WhatsApp, Fb, Instagram, and so on.) | Requires the most recent model of mSpy. Rooting is usually not required for primary options. |
| Android 13 | Absolutely Appropriate | Name Monitoring, SMS Monitoring, GPS Location, App Exercise, Social Media Monitoring (WhatsApp, Fb, Instagram, and so on.) | Rooting could also be required for sure superior options. Test the mSpy web site for particular necessities. |
| Android 12 | Absolutely Appropriate | Name Monitoring, SMS Monitoring, GPS Location, App Exercise, Social Media Monitoring (WhatsApp, Fb, Instagram, and so on.) | Performance much like Android 13, with potential for some superior options requiring rooting. |
| Android 11 | Absolutely Appropriate | Name Monitoring, SMS Monitoring, GPS Location, App Exercise, Social Media Monitoring (WhatsApp, Fb, Instagram, and so on.) | Rooting could also be wanted for some superior options, particularly associated to accessing system-level knowledge. |
Knowledge Assortment Strategies
mSpy’s performance hinges on its capacity to assemble a wealth of data from the goal Android gadget. This knowledge assortment course of is multifaceted, encompassing name logs, textual content messages, location knowledge, and interactions throughout numerous social media platforms. Understanding how these assortment strategies operate is essential to greedy the software program’s capabilities.
Name Log Assortment
mSpy’s name log assortment operates by discreetly accessing the gadget’s name historical past. This contains particulars such because the telephone quantity or contact title, the length of the decision, and the date and time it occurred. The software program successfully creates an in depth file of all incoming, outgoing, and missed calls.
Textual content Message Interception
The interception of textual content messages, each SMS and people from different messaging purposes, is one other core operate. mSpy works by mirroring or duplicating the messages as they’re despatched and acquired. This offers the person entry to the content material of the messages, together with textual content, photographs, and different attachments. The software program’s capability extends to varied messaging apps, which boosts its monitoring capabilities.
Location Knowledge Monitoring
Monitoring the gadget’s location is achieved via using GPS and different location providers, resembling Wi-Fi positioning and cell tower triangulation. This course of offers the person with real-time location knowledge, in addition to a historical past of the gadget’s actions. This characteristic is especially helpful for monitoring the whereabouts of the gadget.
Social Media Knowledge Gathering
mSpy can collect knowledge from a variety of social media platforms. The precise forms of knowledge collected differ relying on the platform however usually embody:* Posts: The software program captures the content material of posts made by the goal person.
Messages
Direct messages and chats are recorded, permitting the person to view conversations.
Shared Media
Pictures and movies shared on the platform are additionally accessible.
Consumer Profiles
Info from person profiles, resembling names, bios, and profile footage, is collected.This functionality offers a complete overview of the goal person’s social media exercise.
Knowledge Varieties Collected from Varied Apps
mSpy’s knowledge assortment extends past primary name logs and messages, encompassing a big selection of data from numerous purposes. Here’s a bulleted checklist illustrating the totally different knowledge sorts mSpy can acquire:* Messaging Apps: Textual content messages, media information (pictures, movies), voice notes, timestamps, contact data, and group chat particulars from apps resembling WhatsApp, Telegram, Sign, and others.
Social Media
Posts, messages, shared media (photographs, movies), profile data, and exercise logs from platforms like Fb, Instagram, Twitter, and TikTok.
E mail
Content material of emails, together with topic traces, sender and recipient particulars, attachments, and timestamps from e-mail apps and webmail providers.
Browser Historical past
Visited web sites, search queries, shopping historical past, and bookmarks from the gadget’s net browser.
Calendar
Calendar entries, together with occasion particulars, attendees, areas, and reminders.
Contacts
Contact names, telephone numbers, e-mail addresses, and different contact data saved on the gadget.
Put in Apps
A listing of put in purposes, together with app names, variations, and set up dates.
Multimedia Recordsdata
Pictures, movies, and audio information saved on the gadget.
Keylogger Knowledge
Information of keystrokes entered on the gadget, together with passwords, search phrases, and typed messages.
Community Exercise
Knowledge associated to community connections, together with Wi-Fi community names, IP addresses, and knowledge utilization.
Options and Performance

mSpy is not only a easy monitoring device; it is a complete digital guardian, providing a collection of options designed to offer insights into a tool’s exercise. From shopping historical past to multimedia information, mSpy unlocks a wealth of data, providing a glimpse into the digital lives of the customers you monitor. Let’s delve into the specifics of what mSpy can do.
Monitoring Web Looking Historical past
Understanding on-line habits is essential in immediately’s digital panorama. mSpy means that you can monitor the web sites visited by the person, offering an in depth shopping historical past.mSpy presents the shopping historical past in an organized format, usually together with:
- Web site URLs visited.
- Timestamps indicating the date and time of every go to.
- Web site titles, giving context to the pages accessed.
This characteristic is invaluable for understanding the person’s on-line pursuits, potential dangers, and general web utilization patterns. As an illustration, if a person repeatedly visits web sites associated to particular matters, it may point out a rising curiosity and even potential vulnerabilities. This data can then be used to foster discussions, provide steerage, or take applicable motion.
Monitoring Put in Functions
Realizing which purposes are put in on a tool is significant for a whole understanding of its utilization. mSpy offers detailed details about all of the purposes put in on the goal gadget.This characteristic usually offers:
- A listing of all put in purposes.
- Software names and icons for straightforward identification.
- Set up dates and instances.
- The flexibility to see the frequency of app utilization.
This functionality is especially helpful for figuring out probably dangerous or inappropriate purposes. It additionally means that you can monitor the person’s app utilization patterns, serving to you to know their digital habits and preferences. Think about the peace of thoughts figuring out what apps your youngster or worker is utilizing, and the way usually.
Distant Management Options
mSpy goes past passive monitoring, providing lively management over the goal gadget. This contains options like web site and utility blocking.This is a breakdown of the distant management capabilities:
- Web site Blocking: You’ll be able to block particular web sites, stopping the person from accessing them.
- Software Blocking: You’ll be able to block using sure purposes.
- Gadget Locking: In some situations, you’ll be able to remotely lock the gadget.
These options empower you to create a safer digital setting. For instance, if a baby is repeatedly visiting inappropriate web sites, you’ll be able to block these websites. If an worker is losing time on social media throughout work hours, you’ll be able to block these purposes throughout enterprise hours.
Accessing Multimedia Recordsdata
The flexibility to entry multimedia information, resembling pictures and movies, saved on the gadget is one other key characteristic of mSpy. This affords a window into the person’s visible experiences and digital interactions.mSpy usually means that you can:
- View pictures and movies saved on the gadget.
- Obtain these information for safekeeping.
- View timestamps and different metadata related to the information.
This performance may be helpful for understanding the person’s social interactions, figuring out potential dangers, or just holding monitor of their digital life. Consider it as a digital picture album, accessible from wherever. As an illustration, you could possibly discover out in case your kids are sharing inappropriate content material or if an worker is taking company-owned gadgets for private use.
Keylogger Function
The keylogger characteristic captures every thing typed on the gadget, offering a complete file of all textual content enter. This could embody messages, emails, search queries, and extra.This is how the keylogger works:
- It data each keystroke made on the gadget.
- It identifies the appliance the place the textual content was entered.
- It means that you can view the typed textual content in a chronological order.
The keylogger may be extremely useful in understanding the person’s communications, figuring out potential threats, or just understanding their on-line habits. For instance, you’ll be able to see the content material of their messages, search queries, and any passwords they could have typed. This data can then be used to guard them from cyberbullying, on-line scams, or different risks.
mSpy’s core functionalities revolve round monitoring web shopping, monitoring put in purposes, distant management, accessing multimedia, and keylogging. These options, mixed, present a complete overview of a tool’s actions.
Stealth Mode and Consumer Expertise
Navigating the digital world requires understanding how monitoring software program operates, particularly regarding its discreetness and its impact on the person expertise. mSpy’s strategy to stealth and its impression on gadget efficiency are vital components in understanding its general performance. Let’s delve into these facets.
Stealth Operation
mSpy is designed to function covertly on the goal gadget. That is achieved via a number of strategies supposed to attenuate the person’s consciousness of the software program’s presence.
- Hiding the Software Icon: Upon set up, mSpy may be configured to cover its icon from the gadget’s app drawer and residential screens. This prevents the person from simply figuring out the appliance.
- Background Operation: The software program runs within the background, constantly monitoring the gadget’s actions with out requiring person interplay. This background course of is optimized to eat minimal sources.
- Notifications and Alerts: mSpy is designed to keep away from sending any seen notifications or alerts that might reveal its presence. This ensures the person stays unaware of the monitoring.
- Course of Masking: The applying’s processes are designed to mix in with different system processes, making it troublesome to establish via typical gadget administration instruments.
Battery Life and Efficiency Influence
The operation of any monitoring software program can probably impression the goal gadget’s battery life and general efficiency. mSpy’s design considers these components to attenuate disruption.
- Useful resource Optimization: mSpy is engineered to make use of minimal processing energy and reminiscence. That is essential for decreasing battery drain.
- Background Synchronization: Knowledge synchronization happens within the background, using environment friendly strategies to switch knowledge with out extreme useful resource consumption. The frequency of information uploads can usually be adjusted to steadiness stealth and battery life.
- Influence on Efficiency: Whereas some efficiency impression is inevitable, mSpy is optimized to make sure that its presence isn’t noticeably affecting the gadget’s responsiveness. The impression is often minor and might not be perceptible to the person throughout common gadget utilization.
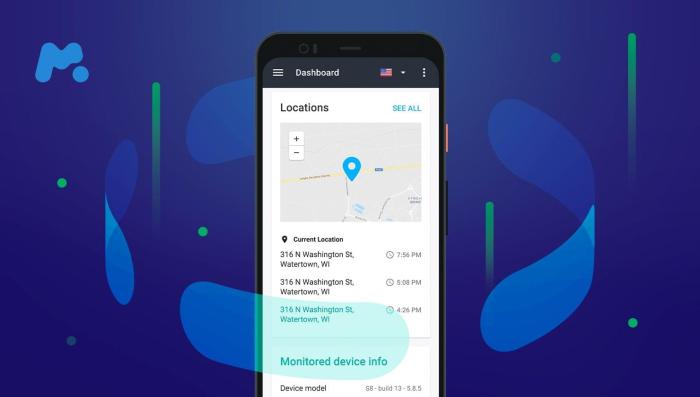
mSpy Management Panel Consumer Interface
The management panel is the central hub for accessing the info collected by mSpy. The person interface is designed to be intuitive and accessible, offering a streamlined expertise for reviewing data.
- Internet-Based mostly Entry: The management panel is web-based, permitting customers to entry the info from any gadget with an web connection, resembling a pc, pill, or smartphone. This offers flexibility and comfort.
- Consumer-Pleasant Design: The interface is designed with ease of use in thoughts, with a clear structure and clear navigation. The objective is to make the collected knowledge simply accessible and comprehensible.
- Knowledge Group: The information is organized into numerous classes, resembling calls, messages, location historical past, and social media exercise. This organized construction permits customers to shortly discover the data they want.
Knowledge Safety Measures
Defending the collected knowledge is a prime precedence for mSpy. The corporate implements a number of safety measures to make sure knowledge confidentiality and integrity.
- Encryption: All knowledge transmitted between the goal gadget and the management panel is encrypted utilizing industry-standard encryption protocols. This prevents unauthorized entry to the info.
- Safe Servers: mSpy makes use of safe servers to retailer the collected knowledge. These servers are protected with strong safety measures to forestall knowledge breaches.
- Entry Controls: Entry to the management panel is restricted to licensed customers solely. Customers should log in with a singular username and password.
- Knowledge Backup and Redundancy: Knowledge is usually backed up and saved redundantly to forestall knowledge loss within the occasion of a system failure.
Management Panel Interface Abstract
The mSpy management panel is a complete interface for reviewing the collected knowledge. The structure and knowledge presentation are designed for readability and ease of use.
- Dashboard Overview: The principle dashboard offers a fast overview of the collected knowledge, together with current actions and key metrics.
- Categorized Knowledge: Knowledge is organized into classes, resembling calls, messages, location, and social media. Every class offers an in depth view of the related data.
- Interactive Charts and Graphs: Knowledge is introduced utilizing interactive charts and graphs to visualise developments and patterns. For instance, location knowledge is likely to be displayed on a map, displaying the goal gadget’s actions over time.
- Search and Filtering: The interface contains search and filtering choices, permitting customers to shortly discover particular data. Customers can seek for particular s, contacts, or time durations.
- Notifications and Alerts: Customers can arrange customized notifications and alerts to be notified of particular actions, resembling incoming calls from a selected quantity or location adjustments.
Compatibility and Gadget Necessities

Earlier than you even take into consideration tapping into the digital lives of others with mSpy, let’s discuss ensuring your Android gadget performs good. Compatibility is essential, and understanding the specifics can prevent a complete heap of bother down the highway. We’re diving into the nitty-gritty of Android variations, root entry, space for storing, and the way it all impacts mSpy’s efficiency.
Android Model Compatibility
mSpy is not a one-size-fits-all sort of deal. It is constructed to work with a variety of Android variations, however not each model is created equal. Understanding which variations are supported is essential for a easy expertise.
This is a breakdown:
- Supported Variations: mSpy usually helps Android variations from 4.0 (Ice Cream Sandwich) as much as the most recent releases. Nonetheless, particular characteristic availability can differ relying on the Android model.
- Older Variations: Whereas mSpy might technically work on older Android variations, performance may be restricted. Options won’t be as complete, and updates is likely to be much less frequent.
- Latest Variations: Holding mSpy up-to-date with the most recent Android releases is a precedence. This ensures compatibility and leverages new options and safety enhancements.
The Root Entry Conundrum
Root entry is a technical time period that may sound a bit intimidating, but it surely’s necessary to know when utilizing mSpy. It mainly means gaining administrator-level permissions on an Android gadget.
This is the lowdown:
- Rooting Requirement: Some superior mSpy options, like monitoring particular apps or accessing deleted knowledge, require the goal gadget to be rooted. Consider it like needing a particular key to unlock a selected door.
- Why Rooting Issues: Rooting offers mSpy deeper entry to the gadget’s inside workings, permitting it to gather extra complete knowledge.
- Rooting is Non-obligatory: Many mSpy options operate completely tremendous with out root entry. It actually is dependent upon what you wish to monitor.
The Influence of Rooting
Rooting, whereas highly effective, is not with out its potential downsides. It is essential to know the implications earlier than taking the plunge.
- Safety Implications: Rooting can probably weaken the gadget’s safety. It opens the door to vulnerabilities if the person is not cautious about what they set up. Consider it like eradicating the locks in your entrance door.
- Guarantee Issues: Rooting can typically void the gadget’s guarantee. All the time examine the producer’s coverage earlier than continuing.
- Gadget Stability: Incorrect rooting procedures can result in gadget instability and even bricking (rendering the gadget unusable). Following directions rigorously is paramount.
Storage House Calls for
mSpy, like several app, wants space for storing to operate successfully. It isn’t an enormous reminiscence hog, but it surely’s good to concentrate on the necessities.
- Set up Measurement: The preliminary set up measurement of mSpy is comparatively small, normally beneath 20MB.
- Knowledge Storage: The quantity of storage utilized by mSpy for knowledge assortment is dependent upon the extent of exercise on the goal gadget. Heavy utilization of messaging apps, social media, and different options will enhance storage wants.
- Suggestions: Make sure the goal gadget has not less than 50MB of free space for storing for optimum efficiency. Commonly clearing cached knowledge on the goal gadget also can assist.
Function Compatibility Desk
This desk exhibits which mSpy options can be found on totally different Android variations, offering a transparent view of compatibility.
| Function | Android 4.x – 5.x | Android 6.x – 9.x | Android 10.x – 12.x | Android 13+ |
|---|---|---|---|---|
| Name Monitoring | Sure | Sure | Sure | Sure |
| SMS Monitoring | Sure | Sure | Sure | Sure |
| GPS Location Monitoring | Sure | Sure | Sure | Sure |
| Social Media Monitoring (Rooted) | Sure | Sure | Sure | Sure |
| Social Media Monitoring (Non-Rooted) | Restricted | Restricted | Restricted | Restricted |
| Keylogger | Sure | Sure | Sure | Sure |
| Deleted Knowledge Retrieval (Rooted) | Sure | Sure | Sure | Sure |
| App Blocking | Sure | Sure | Sure | Sure |
Authorized and Moral Concerns
The usage of monitoring software program like mSpy on Android gadgets raises a posh net of authorized and moral issues. Navigating this panorama requires cautious consideration of privateness legal guidelines, person rights, and the potential for misuse. Understanding these facets is essential to make sure accountable and lawful utility of such expertise.
Authorized Implications of Utilizing mSpy on Android Units, How does mspy work on android
The legality of utilizing mSpy hinges on jurisdiction and the context of its use. In lots of areas, monitoring a tool with out the proprietor’s specific consent is against the law. This usually falls beneath privateness legal guidelines that defend people from surveillance. These legal guidelines differ considerably; for instance, some nations have stricter rules concerning knowledge assortment and utilization than others. Utilizing mSpy to observe a tool you don’t personal, or with out correct consent, may result in extreme penalties, together with civil lawsuits and legal costs.
Moral Concerns Related to Utilizing This Kind of Software program
Past the authorized boundaries, moral issues play an important function. The usage of mSpy includes the potential for violating a person’s proper to privateness and autonomy. Monitoring somebody’s digital life, together with their communications, location, and on-line actions, raises elementary questions on belief and respect. It is important to think about the impression on the monitored particular person’s relationships, psychological well-being, and general sense of safety.
The potential for misuse, resembling stalking or harassment, provides one other layer of moral complexity.
Pointers on Acquiring Consent Earlier than Monitoring a Gadget
Acquiring knowledgeable consent is paramount earlier than putting in and utilizing mSpy. The consent have to be freely given, knowledgeable, and particular.
“Knowledgeable consent” means the particular person being monitored understands what knowledge might be collected, how it is going to be used, and for a way lengthy.
For instance, a mother or father would possibly inform their youngster about monitoring their telephone for security causes, clearly outlining the info collected and its function. This requires open communication and transparency. In a office state of affairs, workers needs to be made conscious of monitoring practices, together with the forms of knowledge collected and the circumstances beneath which it is going to be accessed. Written consent, the place attainable, offers a transparent file of settlement and helps keep away from misunderstandings.
Detailing the Potential Penalties of Unauthorized Monitoring
Unauthorized monitoring carries vital dangers. The monitored particular person can file a lawsuit, resulting in monetary penalties and reputational injury for the person of mSpy. Moreover, relying on the jurisdiction and the character of the collected knowledge, unauthorized monitoring can result in legal costs, together with invasion of privateness and even cyberstalking. Past authorized repercussions, there are additionally moral penalties. The act of secretly monitoring somebody can erode belief and injury relationships, resulting in social and emotional misery for all events concerned.
Authorized and Moral Dos and Don’ts of Utilizing mSpy
To assist navigate the authorized and moral complexities, right here’s a information to what it is best to and should not do when utilizing mSpy:
- Do: Acquire specific consent from the gadget proprietor earlier than set up. This consent needs to be documented, if attainable.
- Do: Clearly talk the aim of the monitoring. Clarify why the monitoring is important and what knowledge might be collected.
- Do: Respect the privateness of the monitored particular person. Solely acquire knowledge that’s vital for the acknowledged function.
- Do: Use the info responsibly. Keep away from sharing the collected data with unauthorized third events.
- Do: Adhere to all relevant privateness legal guidelines and rules in your jurisdiction. Keep knowledgeable about any adjustments to those legal guidelines.
- Do not: Monitor a tool with out the proprietor’s data or consent. It is a direct violation of privateness rights.
- Do not: Use the software program for malicious functions, resembling stalking, harassment, or blackmail.
- Do not: Gather extra knowledge than is important for the acknowledged function. Extreme knowledge assortment can increase privateness issues.
- Do not: Share the collected knowledge with unauthorized people or organizations. Defend the confidentiality of the data.
- Do not: Ignore privateness legal guidelines and rules. Failing to adjust to these legal guidelines can result in authorized penalties.
Troubleshooting and Frequent Points
Typically, even probably the most subtle expertise hiccups. When coping with mSpy, understanding diagnose and repair issues is essential. This part offers a sensible information to deal with widespread points, making certain a easy and efficient monitoring expertise. Let’s dive into some sensible options.
Software Malfunctions
If mSpy is not behaving as anticipated, do not panic! Right here’s a structured strategy to troubleshoot the appliance’s efficiency.
- Test Web Connection: Make sure the goal gadget has a steady web connection (Wi-Fi or mobile knowledge). Knowledge transmission is important for mSpy to operate. Confirm the gadget’s web settings and connectivity. For instance, open an internet browser on the goal gadget and attempt to load a web site. If it fails, the web connection is the seemingly wrongdoer.
- Restart the Gadget: A easy restart can usually resolve minor software program glitches. This clears the gadget’s reminiscence and may refresh the appliance. Energy off the goal gadget utterly, anticipate just a few seconds, after which flip it again on.
- Confirm Software Standing: Test if the mSpy utility is working within the background. Some gadgets have process managers the place you’ll be able to view working purposes. If mSpy is not listed, it may need crashed or been closed.
- Reinstall the Software: As a final resort, reinstalling mSpy can repair corrupted information or configuration points. Uninstall the appliance from the goal gadget after which reinstall it following the unique set up steps.
- Contact Help: If the issue persists, contact mSpy’s buyer assist. Present detailed details about the problem, together with error messages, gadget mannequin, and working system model. Their experience might help resolve complicated issues.
Knowledge Synchronization Points
Knowledge synchronization is the spine of mSpy’s performance. When knowledge would not replace, it may be irritating. Right here’s get issues again on monitor.
- Test Web Connectivity: As beforehand talked about, a dependable web connection is essential for knowledge synchronization. Make sure the gadget is related to the web.
- Confirm mSpy Software Standing: Make sure the mSpy utility is working and has permission to entry the web. Some gadgets have knowledge utilization restrictions that might stop the appliance from synchronizing knowledge.
- Test the Management Panel: Log into your mSpy management panel to see the final knowledge replace. This helps decide if the problem is with the gadget or the account.
- Restart the Software: Restarting the mSpy utility on the goal gadget can typically provoke a brand new synchronization course of.
- Test Gadget Storage: If the goal gadget’s storage is full, it could hinder the appliance’s capacity to retailer and ship knowledge. Clear some area on the gadget by deleting pointless information or purposes.
- Replace the Software: Be sure to have the most recent model of mSpy put in. Updates usually embody bug fixes and efficiency enhancements that may resolve synchronization issues.
Battery Drain Issues
Extreme battery drain is a typical concern. Right here’s deal with potential battery drain points related to mSpy.
- Optimize Settings: Evaluation the appliance’s settings on the goal gadget. Some options, like extreme location monitoring frequency, can eat extra battery. Alter the settings to discover a steadiness between monitoring and battery life.
- Test Software Updates: Make sure the mSpy utility is updated. Newer variations usually embody optimizations that scale back battery consumption.
- Monitor Software Utilization: Use the gadget’s battery utilization monitor to see how a lot energy mSpy is utilizing. This might help establish if the appliance is the first explanation for the battery drain.
- Scale back Monitoring Frequency: If the gadget’s battery life is considerably affected, take into account decreasing the frequency of information updates or location monitoring.
- Gadget Compatibility: Affirm the gadget meets the minimal system necessities for mSpy. Older or underpowered gadgets might battle to run the appliance effectively, resulting in sooner battery drain.
Set up Issues
Set up errors can happen, however they’re usually solvable. This is sort out widespread issues throughout set up.
- Test Compatibility: Confirm that the goal gadget is appropriate with mSpy. The applying’s web site offers an inventory of supported gadgets and working system variations.
- Guarantee Adequate Storage: Make sure that the goal gadget has sufficient free space for storing to put in the appliance.
- Disable Safety Software program: Briefly disable any safety software program (antivirus, and so on.) on the goal gadget, as it’d intrude with the set up course of. Keep in mind to re-enable it after set up.
- Observe Set up Directions: Fastidiously comply with the set up directions offered by mSpy. Any deviation can result in errors.
- Test Web Connection: Make sure the goal gadget has a steady web connection throughout set up.
Troubleshooting Set up Errors:
- Error Message: “Set up failed” or comparable.
- Resolution: Double-check compatibility, unlock space for storing, disable safety software program, and guarantee a steady web connection.
- Error Message: “Software not put in.”
- Resolution: Confirm the set up file, examine for conflicts with different purposes, and guarantee enough gadget permissions.
- Error Message: “Parse error.”
- Resolution: Obtain the set up file once more, because it is likely to be corrupted.
